Bitcoin is the world's first so-called "cryptocurrency", as it is the first currency that is secured by cryptographic procedures and only works thanks to so-called "cryptography". In two previous articles in our"Blocktrainer 1×1"(Article 1, Article 2) we have already discussed what money and a currency are. But what exactly is "cryptography"? In this article of our"Blocktrainer 1×1", we want to briefly explain what it is all about.
Cryptography (from Greek: κρυπτός, kryptós, "hidden", and γράφειν, gráphein, "to write") is the application of mathematical processes to develop techniques and algorithms that protect the security of information.
Accordingly, cryptography is the science of encrypting information and, alongside cryptanalysis, which is the science of decrypting secret messages, forms one of two sub-areas of cryptology.
We've all been there: you're on vacation and write a postcard to family, friends or acquaintances. However, you would probably never write confidential information on a postcard, as you are aware that anyone involved in sending or transporting the postcard may be able to read it.
To prevent third parties from reading the postcard, you can, for example, put the postcard in an envelope and seal it. The recipient then simply has to remove the card from the sealed envelope and can start reading it.
The procedure is similar with today's more modern ways of disseminating information.
With the help of so-called encryption methods, messages can be encrypted in a similar way to the envelope and initially made unreadable. The recipient knows the appropriate method for decrypting the message and can make the message readable again.
The need for confidential communication has existed since time immemorial. Over the course of time, people have come up with very different and increasingly sophisticated methods of encrypting messages.
Unfortunately, in the 21st century, the age of the Internet, computer viruses and "digital signatures", nobody can be one hundred percent sure that the message contains what it claims to contain, or that the sender is who he appears to be. Procedures that guarantee this are called authentication or authentication procedures.
A distinction must be made between subscriber authenticity and message authenticity.
The former is given if a participant (a person) can prove his identity beyond doubt, while message authenticity only exists if a recipient can convince himself without any doubt of the origin of a message and recognize changes to it.
The most important and probably best-known examples of subscriber authenticity, or subscriber authentication as the process is called, are PIN entry on cell phones and ATMs. The correct key combination convinces the device of the identity of the owner.
Similar to handwritten documents, whose authenticity is verified by a signature, so-called digital signatures certify the authenticity of a digital message and thus guarantee message authenticity.
In addition to verifying theauthenticityhowever, modern cryptography has set itself 4 further goals, whereby cryptographic procedures do not necessarily serve all of these goals.
In addition to maintaining authenticity, it is sometimes desirable for the content, sender or recipient of a message, or even the fact of communication between the two themselves, to remain hidden from others. This is referred to asanonymity.
Fromcommitmentis when a subscriber A sends a message to another subscriber B and the latter can then clearly prove to third parties that the message originated from A. In contrast to authenticity procedures, where B can verify the identity of the sender but cannot necessarily prove this to third parties, this method goes one step further.
Another protection goal in the field of information security isintegrity.
This means that data should be complete over a certain period of time and cannot be changed unnoticed. In technical applications, integrity can be checked, for example, by using a checksum, which is also transmitted and shows whether data has been changed.
The last of the 5 goals of modern cryptography is to achieveconfidentiality. This is achieved cryptographically by the sender changing his message in such a way that it appears to be absolutely illogical to third parties. Only the recipient can decipher the original text by means of secret additional information, the so-called "key".
Apart from these newer methods that modern technology brings with it, the focus of cryptography should still be on the simple secrecy of information.

In the modern age, where technology dominates most of our lives, cryptography plays an indispensable role. Yet it is older than you might expect. The beginnings of the art of creating secret messages date back to early antiquity.
Back then, around 2000 BC, ancient Egyptian scribes used unusual hieroglyphs to encode religious texts. The main motive for encryption was the taboo on pronouncing various deities. As this also applied to the written language, it prompted the scribes to use other hieroglyphs.
In later phases of antiquity, however, more sophisticated methods were developed to encode messages.
The ancient Greeks used the so-called scytale (Greek "scytale"; σκυτάλη, "stick", "staff"), a cylindrical wooden stick around which an inscribed parchment or leather strap was wrapped.
The author wrote his message along the staff and then unwound the parchment again. The tape was now sent without the staff. If the tape fell into the wrong hands, it would only show a meaningless sequence of letters. Only someone with a cylinder of the right diameter would be able to read the message.
Probably the most famous encryption technique of antiquity goes back to the most famous general in history: Gaius Julius Caesar (100-44 BC).
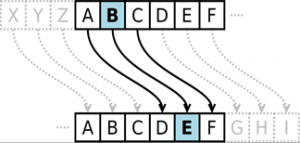
The so-called Caesar cipher (also known as Caesar shift, shift cipher or "simple Caesar") is a particularly simple case of monoalphabetic substitution, as only one fixed key is used to encrypt a message.
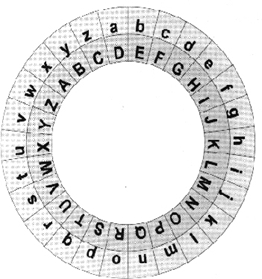
This involves shifting the alphabet by a certain number of letters in order to obtain a new text. Caesar himself often used the key "C", i.e. a shift of 3 letters. The A became a D, the B an E and so on.
As the secret alphabet can also be generated by rotation, i.e. a cyclical shift, instead of a linear shift, it is often referred to as a "rotating alphabet". In the case of "key C" described above, the walking alphabet is referred to as "ROT3" (= rotation by three letters). The word "BLOCKTRAINER", for example, would then become the series of letters "EORFNWUDLQHU" in "ROT3".
The importance of cryptography in ancient times is also made clear by the fact that encryption was defined as one of a total of 64 arts that a woman should master, according to the Kamasutra (Indian erotic book that was probably written in the 3rd century) ☺.
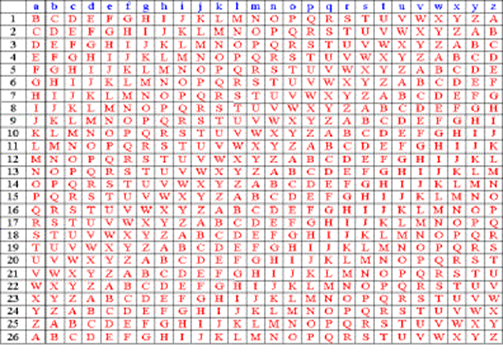
During the period between the years 500 and 1400, only a few new encryption techniques were developed in the European cultural sphere. Simple forms of cryptography, such as the use of a different alphabet or the omission of vowels, were among the most common methods. A real innovation only came with the end of the Middle Ages and the emergence of the so-called Vigenére cipher, which was named after the French diplomat Blaise de Vigenére (1523 - 1596). He developed the first polyalphabetic substitution based on the ideas of the Benedictine monk Johannes Trithemius (1462-1516). In contrast to the Caesar cipher described above, which is a monoalphabetic substitution, Vignére uses more than one alphabet to encode different letters. This means that up to 26 different alphabets are used alternately, depending on the key. Unlike the simple Caesar, where a plaintext letter was always assigned the same ciphertext letter during the course of the text, different ciphertext letters can now mean one and the same plaintext letter.
First you have to think of a keyword. In our example, we choose the word "BITCOIN". For the plain text message, i.e. the text to be encrypted, we select "WE ARE SATOSHI". Now we write down the key and the plain text above and below each other.
B I T C O I N B I T C O I N
W E ARE S A T O S H I
The so-called Vigenére square is now used for encryption, whereby it should be mentioned that the letters J and V were missing in the original, as no distinction was made between I and J or U and V at that time.
At the end of the 19th century, in 1883 to be precise, the Dutch linguist and cryptologist Dr. Auguste Kerckhoffs (1835 - 1903) wrote his famous Kerckhoff's principle (also known as Kerckhoffs' maxim), which was named after him. He set a total of six requirements for an encryption method, whereby the second of the six is usually referred to when talking about Kerckhoff's principle.
The six principles he formulated are as follows:
Unfortunately, a cipher system that met these requirements did not exist at the time. However, Kerckhoff's principles are unmistakably important for today's modern cryptography. They are used in many so-called public key procedures, because nowadays it is usually more difficult to keep an algorithm secret than a key. Moreover, history has shown that methods that were kept secret by their developers were usually relatively weak and insecure.
At the beginning of the 20th century and with the outbreak of the two world wars, radio communication also became increasingly important. As a result, new demands were also placed on encryption methods and the first encryption machines were developed.
In the years that followed, various companies developed encryption machines, two of which became particularly famous:
Firstly, the "ENIGMA" cipher system developed by the German electrical engineer Arthur Scherbius (1878 - 1929) and secondly, the "Schlüsselgerät 41" (better known as the "Hitlermühle") used by the Germans, towards the end of the Second World War.
Even today, encryption is still done by machines, namely computers. Since computers are particularly good at simply trying out different ways of solving a problem, more sophisticated ways of encrypting messages have to be found today. If your Bitcoin balance was only secured with a "simple Caesar", a fraudster with a modern computer would not need a second to rob you of your money. However, as it would clearly go beyond the scope of this article if we were to go into detail about individual modern cryptographic methods, I will cut this a little short. We will be happy to go into this in a later article.
In general, encryption methods can be divided into 2 groups. Insymmetricandasymmetricencryption. The latter is often referred to as "public key cryptography" and is used in the Bitcoin network, among others.
Symmetric encryption methods use the same key for both encrypting and decrypting a message. The security of this system is therefore based entirely on the secrecy of the key (see "Kerckhoff's principle").
In contrast to symmetric methods, asymmetric encryption methods use two different keys. A public key is used to encrypt a message and a private key is used to decrypt the message.
This asymmetric system can be compared to posting a letter in a letterbox. Posting the message corresponds to encrypting it with the recipient's public key. The recipient is the only one able to open the letterbox and read the message using his private key.
Using Bitcoin as an example, or in the world of cryptocurrencies in general, you will often come across the two terms publicand private key. Someone can send money to a public address (public key) and only the person who has the corresponding private key can dispose of it. For this reason, you should always make sure that you are the only person who knows the private key associated with your cryptocurrencies!
The field of cryptography is omnipresent today and has become an integral part of our everyday lives, even if many users are unaware of it. As the security of encrypted systems is of ever-increasing importance, people are constantly on the lookout for new, even better methods. After all, cryptanalysis is also becoming ever more advanced and faster.
However, the computers used for encryption are also constantly improving and the focus of many scientists is currently on the development of a quantum computer. This would then (allegedly) be able to try out all possible combinations and cases in a fraction of a second, meaning that all systems encrypted using non-quantum-safe algorithms could be cracked using brute force (=stubborn trial and error). Whether quantum computers could also pose a threat to Bitcoin will also be discussed in a later article.
However, it must be said that this extreme performance of a supercomputer is also offset by so-called quantum cryptography. This is based on Heisenberg's uncertainty principle, which states that every measurement on a quantum mechanical system causes a disturbance in the system. If it is now possible to generate a data stream that immediately indicates every possible measurement, i.e. every eavesdropping attempt, or destroys itself or makes itself unreadable, eavesdropping is virtually impossible. Unfortunately, an encryption system that is absolutely tap-proof and unbreakable for all time will probably remain a utopian dream of mathematicians and cryptographers.
If you liked this article, you might also be interested in this one: "What is mining?"
You are also welcome to join our free forum.blocktrainer.de and let us know what you think.