Digital information has no value in terms of its uniqueness. All data stored on a hard disk, for example, can be duplicated as often as you like without much effort - without being able to tell the difference between the original and the copy.
What is normally extremely practical turns out to be a fundamental problem as soon as you want to create purely digital money. After all, there has to be some way of preventing it from being copied and thus spent twice. This characteristic of digital money is known as the double-spending problem and, at least in theory, cannot be solved.
Probably the simplest way to prevent double spending is to introduce a central controlling authority, such as a bank, which decides for each transaction whether it may be carried out or not. This works well until the central authority uses its power in some way, either of its own volition or because it is forced to do so. Censorship of transactions, account closures or even expropriation are the inevitable result sooner or later.
A decentralized alternative that cannot be directly controlled by anyone and is resistant to censorship and manipulation seems almost impossible at first glance. But only at first glance.
In October 2008,Satoshi Nakamoto presented a mechanism for a decentralized, purely digital payment network with the Bitcoin white paper, and thus also an approach to solving the double-spending problem. Proof-of-work mining is intended to ensure that nobody can carry out double spending and that retroactive changes to the transaction history are virtually impossible. But how exactly is this supposed to work?
Analogies are always used to explain Bitcoin mining. It starts with the name itself. Although the comparison to traditional gold mining is far too imprecise for an in-depth understanding, it nevertheless conveys a fundamental characteristic: finding new Bitcoin is increasingly associated with high effort and costs. But that's where the analogy ends. The overarching purpose of Bitcoin mining is not to find new Bitcoin, but to ensure the security of the network.
Gold is a rare and therefore scarce resource. Everyone knows this almost as a law of nature; after all, scarcity is nothing unusual in the real world. The opposite is true in the digital world. As shown at the very beginning of the example, money cannot exist digitally in "file format", at least not without preventing any duplication. Accordingly, there are no "bitcoins" lying around on computer hard disks like gold bars.
The Bitcoin network is an association of thousands of computers that all agree on a set of rules. They not only agree on these rules, but also on the history of all past transactions, which in turn naturally fulfill these rules.
The transactions are summarized in data blocks and linked together chronologically. This is where the infamous buzzword "blockchain" comes into play. Contrary to what is often portrayed, however, a blockchain is not an exciting innovation, but rather a means to an end. The principle of linking data blocks together so that changes to one block continuously affect all subsequent blocks was already being used in various areas of IT and cryptography before Bitcoin.
Instead, the innovation lies in the mechanism that decides when a new block may be added to the blockchain and which chain is the valid one. Proof of Work enables precisely this. Without a central intermediary, solely with the help of mathematics and game-theoretical incentives.
Explaining Bitcoin mining on a technical level is the only way to combine all the important aspects in order to provide a deep and complete understanding. Nevertheless, we will first approach the topic using an analogy. To do this, we will avoid the common stories of solving Sudokus and lottery games, because there is a much better one: a simple dice game!
In the following, we will take a look at the process that determines when a miner has "found" a valid block, is allowed to add it to the existing chain and receive a reward for doing so.
Let's imagine a 1000-sided cube as an example. In practice, such a dice would probably be somewhat unwieldy, but we are not in the digital world for nothing, where generating random numbers between 1 and 1000 is no problem.
To win the game, a number must be rolled that is smaller than a target value set by the game master. For example, let's simply set this to the number 10. All players now start rolling the dice diligently until someone is lucky and rolls a number between 1 and 10.
A player, let's call her Alice, can now increase her chances of winning by rolling the dice more often. Although the probability per roll always remains the same in this case, the more often the dice are rolled, the higher the probability of rolling a valid number within a certain period of time.
Alice doesn't play the game alone, however, as that would be pretty boring. Sooner or later, all the other players come up with the idea of increasing the number of dice thrown per second in order to keep up with Alice. The game is won much more often because the dice are rolled more often in the same amount of time. At some point, the game becomes too easy.
Fortunately, the game master can easily adjust the difficulty of the game by changing the target value. If he increases it, the game becomes easier. If he lowers it, it becomes correspondingly more difficult to roll a valid number:
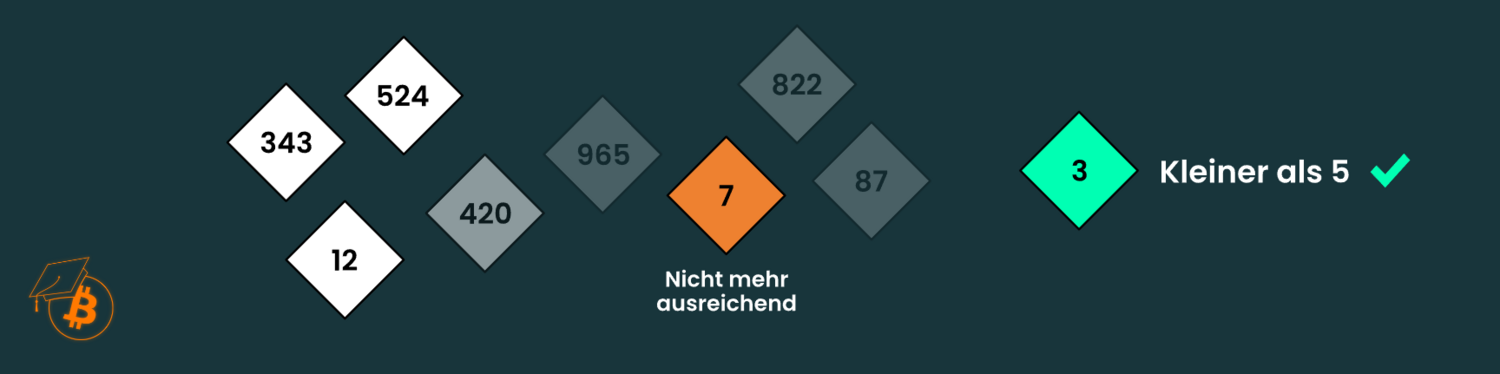
As this game is nothing more than mathematics and probability calculation, the target value can be set very precisely to the desired difficulty. To do this, simply look at the last rounds of the game, i.e. how long it took until a valid number was rolled. If you then want to maintain an average time interval of 10 minutes, for example, you have to increase or decrease the target value accordingly.
In a dice game, you can of course also simply be lucky. No matter how difficult the game may be, you can theoretically win it with a single roll. It's no different in the Bitcoin network. However, in the long term and with a low target value, this also happens extremely rarely.
Unfortunately, our dice game analogy is also slowly reaching its limits. Because while the principle itself can be found in exactly the same way in the Bitcoin network, we still have a problem: What are the dice rolled with? How is it ensured that no one can pretend to have rolled a small number? Even if a small number was actually rolled, how can this be verified? And above all: who determines the target value?
In the Bitcoin network, of course, the dice are not rolled with a dice, but with the cryptographic hash function SHA-256. This function has some special properties that allow us to take the dice game to the extreme.
Unlike a dice, the hash function itself does not generate "random" values, but rather something like a fingerprint. The same input therefore always leads to the same output. You can imagine this as if you knew the exact physical parameters of the throw of a real dice and repeated them. The dice would then theoretically always land on the same result.
Just try it out here and check whether the hash value specified here, i.e. the result from the hash function, actually matches the "block trainer" input:
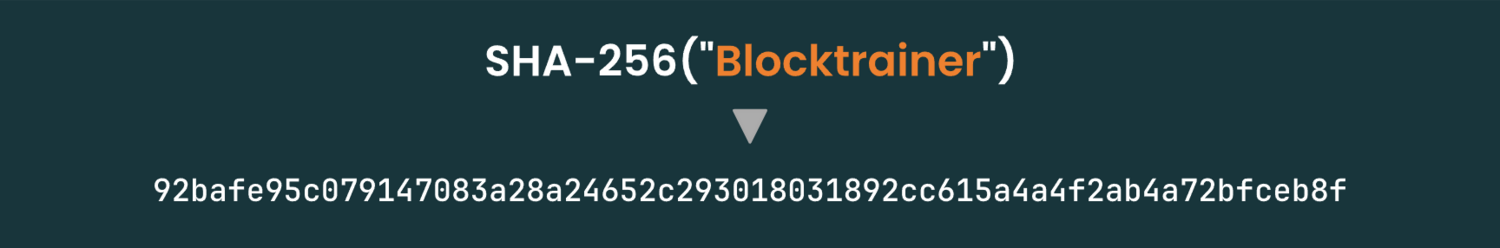
A hash value is nothing more than a rather large number. SHA-256 does not have 1000 pages, but a whopping2256. This number is comparable to the number of atoms in the visible universe.
Three other important properties are
But what are the miners actually doing now? We can now finally answer this question properly!
A miner is initially a normal Bitcoin node, i.e. a participant in the network that receives, verifies and forwards transactions. With these as yet unconfirmed transactions, it now builds something like a block prototype. This prototype has everything that a valid Bitcoin block must have, with one exception: it does not yet have a valid proof of work.
Remember: the result of a hash function is simply a number. The miner chases his block prototype through the hash function and gets a number back, which is the end of an attempt to roll the dice. This is because in the Bitcoin network, as in the dice game, there is also a target value that must be undershot. If the miner has no luck with this attempt, it changes a tiny detail in the block prototype and calculates the hash value again. Again, a number is returned, this time quite small, as can be seen from the leading zeros:
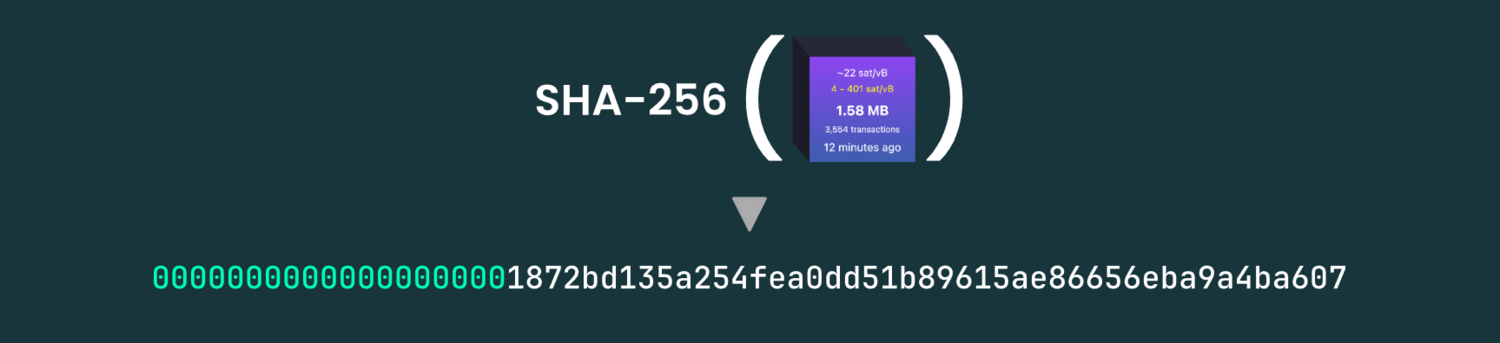
If the block hash fulfills the current rules of the game, the miner has "found" a valid block. They can now publish it on the Bitcoin network. Other participants can in turn calculate the block hash themselves and thus independently verify whether it really falls below the current target value. It is therefore not possible to fake a false hash value, as this ultimately depends on the block itself.
The target value cannot be manipulated either: Every network participant can work it out for themselves by looking at the blocks of the past two weeks. This can be used to determine whether the game is currently too difficult or too easy.
Calculating a single hash value is no problem for a computer. So no "complicated mathematical puzzles" are solved, it simply rolls the dice. Over and over again. To find a valid block after an average of 10 minutes, the Bitcoin network currently needs around 400,000,000,000,000,000,000 attempts every second.
If you retroactively change something in a block, the hash value changes accordingly. So you roll the dice all over again and the proof of work is lost, as you are unlikely to win again on the first attempt.
In addition, all subsequent blocks would also change, as they are linked together. To make a retroactive, valid change to the transaction history, you would therefore have to reroll all blocks since the time of the change. In view of the current difficulty in the Bitcoin network, this is almost impossible after just a few blocks.
Bitcoin miners invest in expensive hardware and require a lot of energy to participate profitably in the dice game. A block with invalid transactions would be rejected by the network despite a valid proof of work. The miner would lose its potential profit and be left with its hardware and energy costs.