Anyone who deals with cryptocurrencies will sooner or later stumble across terms such as hash or hashrate. In today's Blocktrainer 1×1, we want to explain what a hash is and why it is essential for cryptocurrencies.
But first, you should read our "Block trainer 1×1: What is cryptography?". This article will give you a perfect introduction to better understand the following topic.
The name "hash" or "hash function" comes from the English verb "to hash" and means " tochop up". You take a quantity of data and hash and swap it in order to convert it into a different form. The aim of a hash function is to map a large input quantity to a smaller target quantity. The character string that represents the result of this function is called a "hash".
In cryptography, a hash function is also described as a mathematical one-way function. A text can be easily encrypted in one direction using a hash, while the encrypted text is very difficult to convert back into the original text.
On Blocktrainer.de you will find a 9408-word article on
"The bullish case for Bitcoin" byVijay Boyapati.
I now take this text and hash it using SHA-256 (I'll tell you what that is later):
bcec5ca31ba2793b001a7a3de4e035a6b57fb8a72087bb023aa58f7f26d99eb5
Here are some more examples. Observe how small differences change the whole hash.
1) Here is the word "hello", which was hashed using SHA-256.
d3751d33f9cd5049c4af2b462735457e4d3baf130bcbb87f389e349fbaeb20b9
2) Here is the word "Hello", which was hashed via SHA-256.
753692ec36adb4c794c973945eb2a99c1649703ea6f76bf259abb4fb838e013e
3) Here is the word "hello!", which was hashed via SHA-256.
f4facd09fc865aa866b1390e02911b27f599bd52793d3835429862f900b76d6c
No matter what we enter, whether long or short texts, whether we write a word in lower or upper case, whether we add or omit characters, a new individual hash will always be generated, which apparently contains no systematics and has a predefined length (here 64 characters).
If an entity tries to recalculate the original text using a reverse function, it will take a long time, as the recalculation is almost impossible!
With the cryptological hash functions used for cryptocurrencies such as Bitcoin, it must be ensured that each input results in a different output. Otherwise, a so-called hash collision occurs, whereby the corresponding hash algorithm is considered "broken" and insecure (also referred to as a "break" in the hash function).
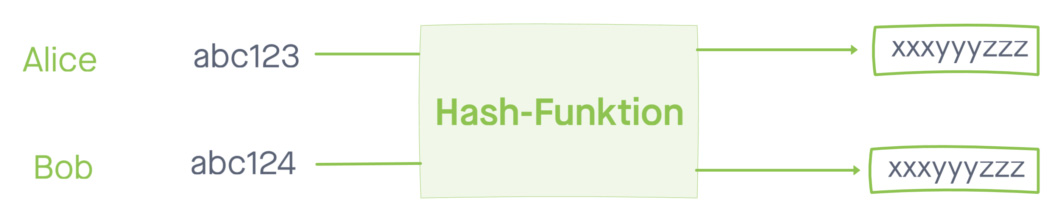
A hash collision is illustrated in the following figure. Alice and Bob have two different inputs, but both receive the hash "xxxyyyzzz" as output.
The most common hash algorithms by far include the SHA-2 family (Secure Hash Algorithm). The SHA-1 group is considered insecure today, as collisions have been discovered several times in the past.
SHA256 is the most widely used hash algorithm. There are also SHA-224, SHA-384 and SHA-512, which all come from the SHA-2 family. The number added after the SHA indicates the length of the hash value in bits.
SHA-256 is still considered secure today. This is due to the fact that a brute force attack* on this function would require an average of 40^38 attempts to guess the input value for a given result. Because this computing power cannot be mustered today, SHA-256 is considered collision-proof for the time being.
*Did youknow: A brute force attack is nothing other than trying out all possible ways of cracking a (e.g. password) one after the other.
Hash functions are required for cryptocurrencies such as Bitcoin, especially during the mining process. This is because the miners try to find a hash that meets predefined requirements or rules.
Did you know: The mining difficulty specifies the requirements for a hash value to be considered valid. The purpose of the difficulty is to ensure that the block time always remains the same, regardless of the computing power in the network.
During the mining process, all that is done is to try out various inputs with a hash function in order to obtain a valid output (hash value) that meets the requirements of the current mining difficulty.
These tasks can be performed using CPUs and GPUs. But there is also special mining hardware (ASICs) that can perform this task particularly efficiently. We have already written an article about ASIC miners in an earlier Blocktrainer 1×1.
A cryptographic hash should have the following five properties:
Do you agree that quantum computers will pose a threat to SHA-256? If "yes", what will happen to Bitcoin in this case? Feel free to write your opinion in our forum.blocktrainer.de and discuss it with us.