In this article, we explain the "Byzantine generals' problem" and why Bitcoin solves it. This is a hypothetical mind game in which several generals have to make a joint decision at the time of the Byzantine Empire.
As the blockchain is not controlled by any central party, the majority of nodes must reach a consensus. They decide what is stored on the decentralized database and what is not.
This requires 2/3 or more of the nodes to act reliably and honestly in order to avoid the complete failure of the network. The hypothetical thought experiment compares the network nodes in a metaphor with Byzantine generals, who behave similarly to the nodes on a blockchain.
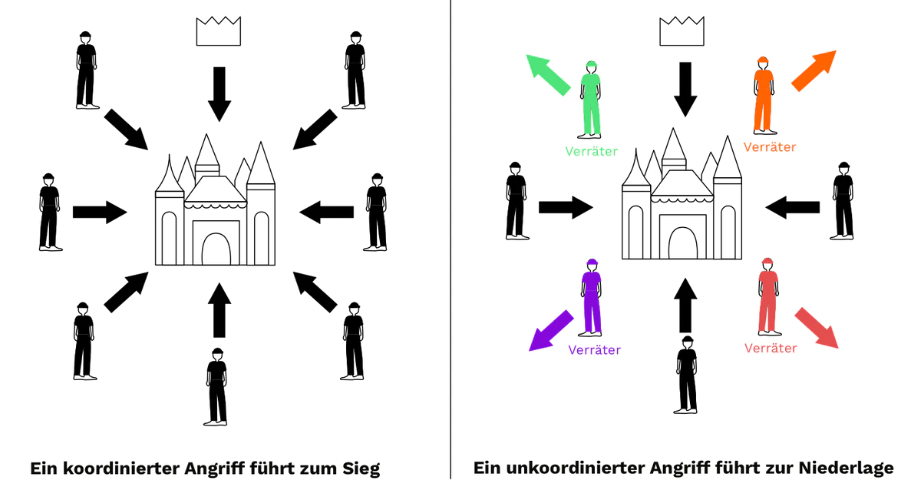
The Byzantine generals' mind game describes a war scenario in which a city is to be conquered. In this scenario, several generals lead the Byzantine army. Each general delegates a part of this army. There is a communication problem between the generals, as each general is in a different location and, of course, there were no cell phones or other means of simultaneous communication at the time (see Figure 1).
The aim of this consideration is that the generals can attack the city or betray their comrades and flee. It is not important which decision they make. They just have to agree on the final decision.
There are certain rules that must be observed when making a decision:
As already mentioned, there were no telephones in the times of the Byzantine Empire. Instead, the generals communicated with each other by courier. This creates points of attack to falsify the message by destroying it, delaying its arrival or losing it in some other way.
A second danger comes from the generals themselves. They could be traitors and send false messages or act maliciously to confuse the other generals.
For example, a blockchain can be attacked by a so-called 51% attack.
In a 51% attack, the majority of the network knowingly acts maliciously to disrupt the system, e.g. by spending coins twice, which would be possible with a 51% majority of the computing power. To prevent such "double spending" from happening, Bitcoin has a security feature known as Proof-of-Work (PoW for short). This implementation tells the network "how the rules must be followed to reach a consensus". Satoshi himself explained how to solve this problem back in 2008 in a forum post using modern Byzantine generals:
"The proof-of-work chain is the solution to the problem of Byzantine generals. I'll try to rephrase it a bit for this context.
A certain number of Byzantine generals have one computer per person and want to attack the king's Wi-Fi by bruteforcing his password, which they know is a certain number of characters long.
Once they get their network to produce a packet of passwords, they only have a limited amount of time to crack the password and delete all the log files, otherwise they would be discovered and get in trouble. They only have enough CPU power to crack the password fast enough if a majority of them are attacking at the same time.They don't particularly care when the attack happens, just that they all match. It was decided that anyone who wants to can announce a time and the time heard first becomes the official attack time. The problem is that the network does not transmit information instantly, and if two generals announce different times at almost the same time, one will hear this one first and the other will hear that one first. To solve this problem, they use a proof-of-work chain.
Once each general receives the attack time he heard first, he has his computer solve an extremely hard proof-of-work problem that contains the attack time in a hash.
The proof-of-work is so difficult that it is expected to take 10 minutes to solve if everyone works on it together. As soon as one of the generals finds a solution, he broadcasts it on the network, and everyone changes the proof-of-work to contain the hash of the solved proof-of-work. If someone was previously working with a different attack time, they change it because the proof-of-work chain is now longer.After two hours, an attack time should be hashed by a chain of 12 proof-of-works. By verifying the difficulty of the proof-of-work chain, each general can see how much parallel CPU power was used per hour for it and whether the majority of computers were used for it. They must have all seen it, as the proof-of-work is the proof that they worked on it. If the CPU power used for the proof-of-work chain is sufficient to crack the password, they can safely attack at the agreed time.
The proof-of-work chain is how all the problems with distributive database synchronization and global visibility problems you talked about are solved.
Satoshi Nakamoto