In this article, we show how the blockchain network is attacked by a Sybil attack and how it can be protected against this.
As described in the "Byzantine Generals Problem", nodes can act maliciously. One way nodes try to cheat the network: They duplicate themselves multiple times in order to gain as much decision-making power with the aim of influencing the democratic consensus. Such an attack is called a Sybil attack.
The term "Sybil" originally comes from the novel of the same name, "SYBIL". In it, the main character Sybil Dorsett suffered from dissociative identity disorder. As this clinical picture is very similar to the cyber attack discussed here, it was named Sybil attack.
The majority (at least 2/3) of all nodes in the blockchain network must act honestly. In our example, we have one traitor and two honest nodes. They have to make a decision. As an example, we have a decision between retreating and attacking. You may already be familiar with this example from our article on the "Byzantine generals' problem".
If all the votes are added up, the result is "attack". Our traitor, on the other hand, wants to enforce the "retreat" decision. So how does he do that?
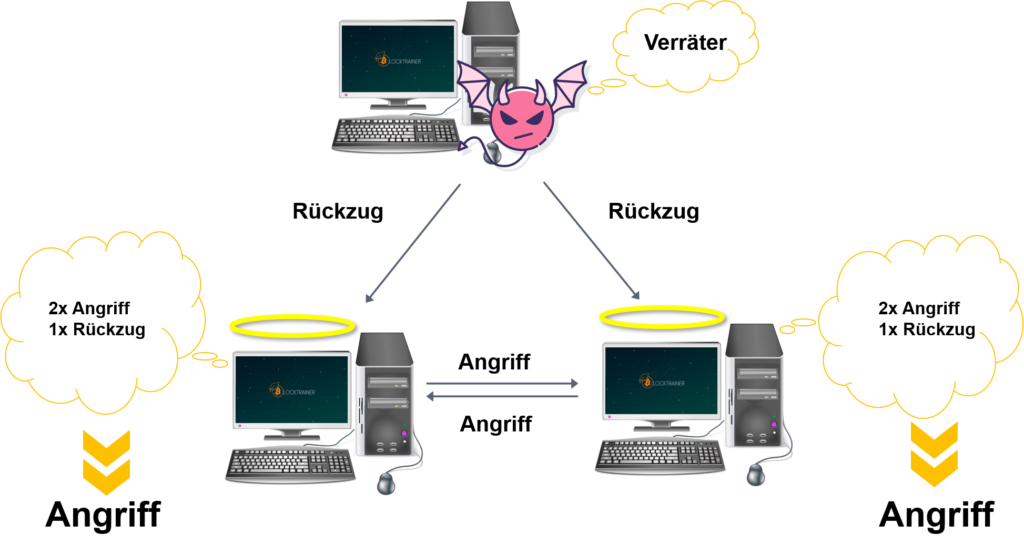
By trying to duplicate its entity and thus its voice, the traitor can corrupt the network. The honest nodes directly receive three messages instead of one (as in the previous example).
This changes the result after the vote count. Instead of "attack", the network now decides to "retreat" and the traitor has achieved his goal.
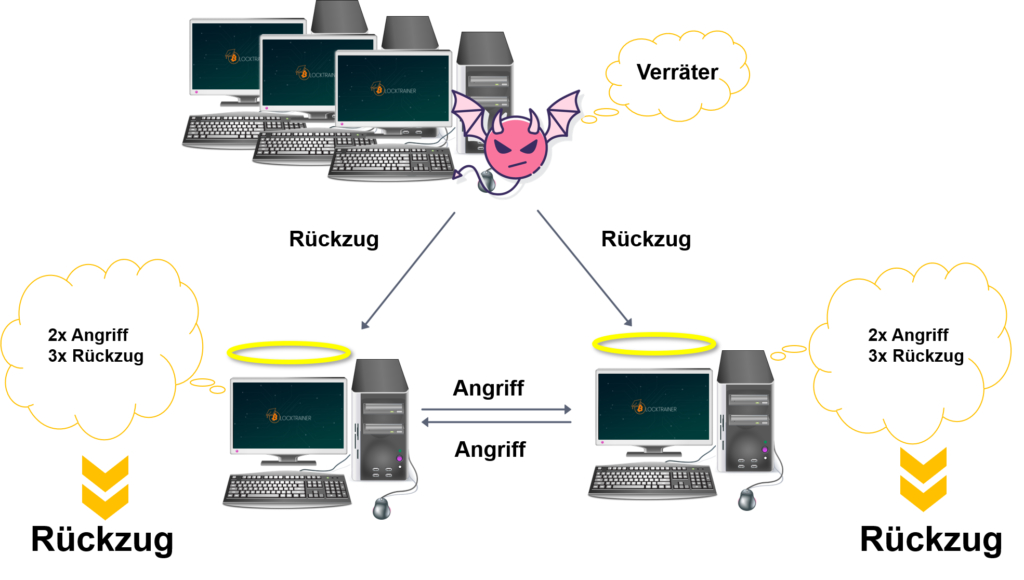
To prevent Sybil attacks, the network must verify that all nodes act in a trustworthy manner and only reflect one vote.
In the real world, elections are held in which every citizen can confirm their identity with their ID card. This means that everyone can only cast one vote. However, this requires a central authority. In this case, the state. This creates the voter lists and distributes the ID cards.
In a blockchain, however, there is no such controlling authority. Instead, a node must prove that it is a genuine participant. To do this, it is checked whether it has the necessary resources to generate a block or whether it has to split them up and thus represent a multiplied identity.
As with Bitcoin, for example, this can be done via a proof of work. To do this, the participant must find new blocks in a mining process and thus prove that they have a certain computing capacity. This computing resource is very expensive due to the high acquisition costs for hardware and ongoing costs for electricity and storage.
Alternatively, the next block producer can be determined via the proof-of-stake. This requires the producer to deposit a "stake" in internal resources (i.e. internal currency) as collateral. As the amount of stakes increases, so does the probability of being allowed to connect the next block. As a lot of internal currency has to be deposited in return, this makes a Sybil attack very expensive.